Dilation Effect Research: A Deep Dive into Mainstream Exchange Account Password Leaks
This article is jointly published by Dilation Effect and WuBlockchain.
Evaluating the security measures of cryptocurrency exchanges is a complex task, as gaining insights into the specifics of their internal security investments can be challenging. Dilation Effect has previously conducted an analysis focusing on smart contract approval, a unique dimension, to scrutinize wallet addresses of top industry exchanges and institutions. This time, we approach the issue from both the attacker’s and the user’s perspectives to analyze the security mechanisms of mainstream exchange accounts, as these directly impact the safety of user funds.
I. Password Leaks in Mainstream Exchange Accounts
We attempted to filter domain names associated with mainstream exchanges using publicly available data breach search websites. Our data sources included the dark web, file-sharing platforms, and historical datasets of leaked account information. It’s worth noting that malicious actors also undertake similar actions.
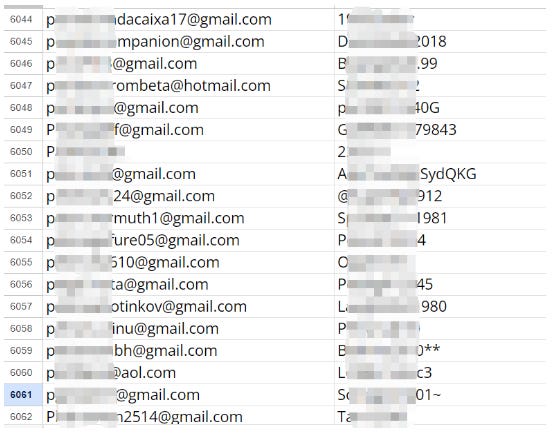
We initiated our investigation with Binance.com and were alarmed to discover over 8,000 plaintext records containing usernames and passwords! Here are some excerpts for illustration:
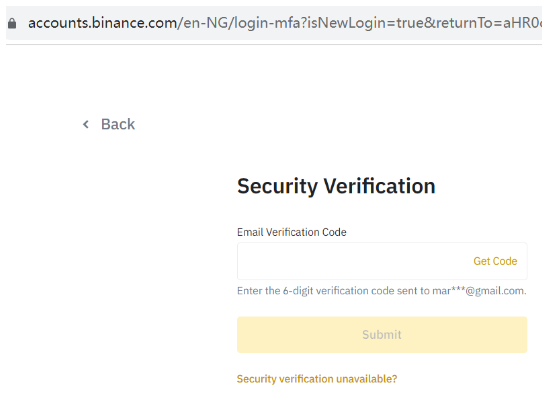
Randomly selecting samples from this data, we attempted to log in and found that numerous account-password pairs were entirely accurate. Some attempts even advanced directly to the two-factor authentication (2FA) stage, as demonstrated by the following example for the account mar*@gmail.com:
If a user’s email account uses the same credentials as their exchange login email, attackers can effortlessly acquire the email verification code needed for 2FA, gaining access to the user’s Binance account. This revelation is startling. It’s important to emphasize that our verification attempts concluded at this point, with no further actions taken.
Dilation Effect conducted preliminary statistics on password leaks for over ten mainstream exchanges, each yielding thousands of records. The magnitude is outlined in the table below:
The scale of the issue is indeed disconcerting.
Due to time constraints, Dilation Effect did not individually verify the accuracy of each leaked account-password pair. However, through random sampling, we discovered that every exchange’s leaked account-password data contained correct entries. We estimate that the initial accuracy rate falls within the range of approximately 10% to 20%.
It’s crucial to note that account and password leaks, in isolation, do not automatically result in financial losses for users. Cryptocurrency exchanges typically offer additional layers of security, such as 2FA mechanisms. Nevertheless, users remain at risk if they have not configured their security settings adequately. For instance, if users exclusively rely on email verification for authentication or if their other authentication factors are compromised.
Next, we delve into the security strength of common 2FA authentication mechanisms.
II. Security Comparison of Common 2FA Mechanisms
Let’s begin with an overview of the security levels associated with various 2FA factors:
Dilation Effect believes that standard user emails exhibit relatively fragile security. Email verification codes are not stable security verification factors. In today’s landscape, if a user relies solely on email verification as their 2FA method, their account’s security can be considered nonexistent. It’s imperative to recognize that major internet service providers have experienced large-scale leaks of usernames and passwords due to attacks. Furthermore, email service providers may harbor unknown vulnerabilities, collectively placing numerous user emails in an insecure state. In summary, the security of email verification is notably low.
SMS verification codes also face vulnerabilities in numerous attack scenarios. These include directed attacks like fake base station assaults, where high-value users might be monitored, allowing attackers to deploy rogue base stations near their targets to intercept SMS messages. Another example is the Sim-swapping attack that Lapsus$hackers like to carry out. SIM swapping involves attackers, often employing social engineering tactics, impersonating users to transfer their SIM cards to the attacker’s name. With the advent of eSIM technology, attackers can apply and activate online, streamlining the process. Twitter founder Jack Dorsey’s Twitter account fell victim to such an attack. Additionally, concerns arise regarding lawful interception by telecommunications providers. Given these scenarios, the security level of SMS verification is relatively low.
In contrast, TOTP (Time-based One-Time Password) and Security Key-based methods face fewer threats. Dilation Effect recommends that users, at the very least, configure Google Authenticator as their fundamental security setting. Users with higher security requirements may opt for physical Security Keys. If a user has exclusively set up email verification or SMS verification, it’s only a matter of time before their account falls prey to attackers.
Furthermore, several exchanges now support passkeys, which represent a robust security mechanism, allowing users to substitute traditional passwords. Users are encouraged to familiarize themselves with these options gradually.
III. Recommendations for Exchanges
Exchanges should immediately initiate emergency response protocols to investigate instances of leaked user account passwords. They should guide affected users to change their passwords and enhance their account security settings. Furthermore, regular monitoring of user account password leaks is essential. For those uncertain about how to identify leaked password data for their users, feel free to reach out to Dilation Effect for assistance(dilationeffect@gmail.com).
We propose that exchanges adopt a “Secure by Default” design approach, prioritizing user account security. This approach ensures that user accounts are in a relatively secure state once security settings are configured. Design principles may include requiring users to complete Google Authenticator binding as a security baseline. By doing so, users can be guided through this setup during registration, and sensitive operations, such as withdrawals, would only be permitted once these settings are in place.
IV. Recommendations for Everyday Users
Respect the importance of network security. Attackers are persistent, while most users have limited knowledge of network security. Even prominent figures like Vitalik have had his X accounts hacked. Users should not neglect their account security settings for the sake of momentarily convenient withdrawals, as regret often follows after an attack. Therefore, users should, at the very least, enable Google Authenticator for their accounts.
Additionally, there is a valuable website where users can periodically check if their email passwords have been compromised, which is worth bookmarking:
https://haveibeenpwned.com
About Dilation Effect
Dilation Effect is a recently established Web3 security community comprising experts in practical network security from around the world. We focus on sharing objective and neutral Web3 security perspectives.
Dilation Effect was the first in the industry to highlight the risk of asset theft when using a shared Apple ID to download wallet apps on iPhones. We have also conducted exclusive analyses and disclosures, including:
Smart contract approval risks for major wallet addresses of top institutions and exchanges like Binance, KuCoin, Jump, and more
Security risks of Prime Protocol, a DeFi cross-chain lending protocol invested in by Jump
Risks brought to lending protocols by using GMX’s GLP and related tokens (mGLP, etc.)
Centralized security risks in Bungee, the most popular aggregated cross-chain bridge protocol in the industry
Dilation Effect will continue to release various Web3 security perspectives, review the security of Web3 products and protocols in the industry, and provide timely and effective security alerts to ordinary users. Follow us on https://twitter.com/dilationeffect.
Follow us
Twitter: https://twitter.com/WuBlockchain
Telegram: https://t.me/wublockchainenglish